Limiting Access to Data
You can limit what data individual users can see and query using Data Permissions and Data Access Roles. Once set, users with Data Access Roles will be able to perform the activities of users with the General:Read permission, but they will see only data they have been granted the access to. This includes all parts of the Platform, including the Asset Inventory, SQL Console, and Reports.
This feature applies only to data synced to CloudQuery Platform. If you sync to an external database, you need to manage the data access yourself.
Data Access Controls Overview
The Data Access Controls consist of:
- Data Permissions: individual permissions granting access to a defined set of data in the CloudQuery Platform Database
- Data Access Roles: containers for individual data permissions
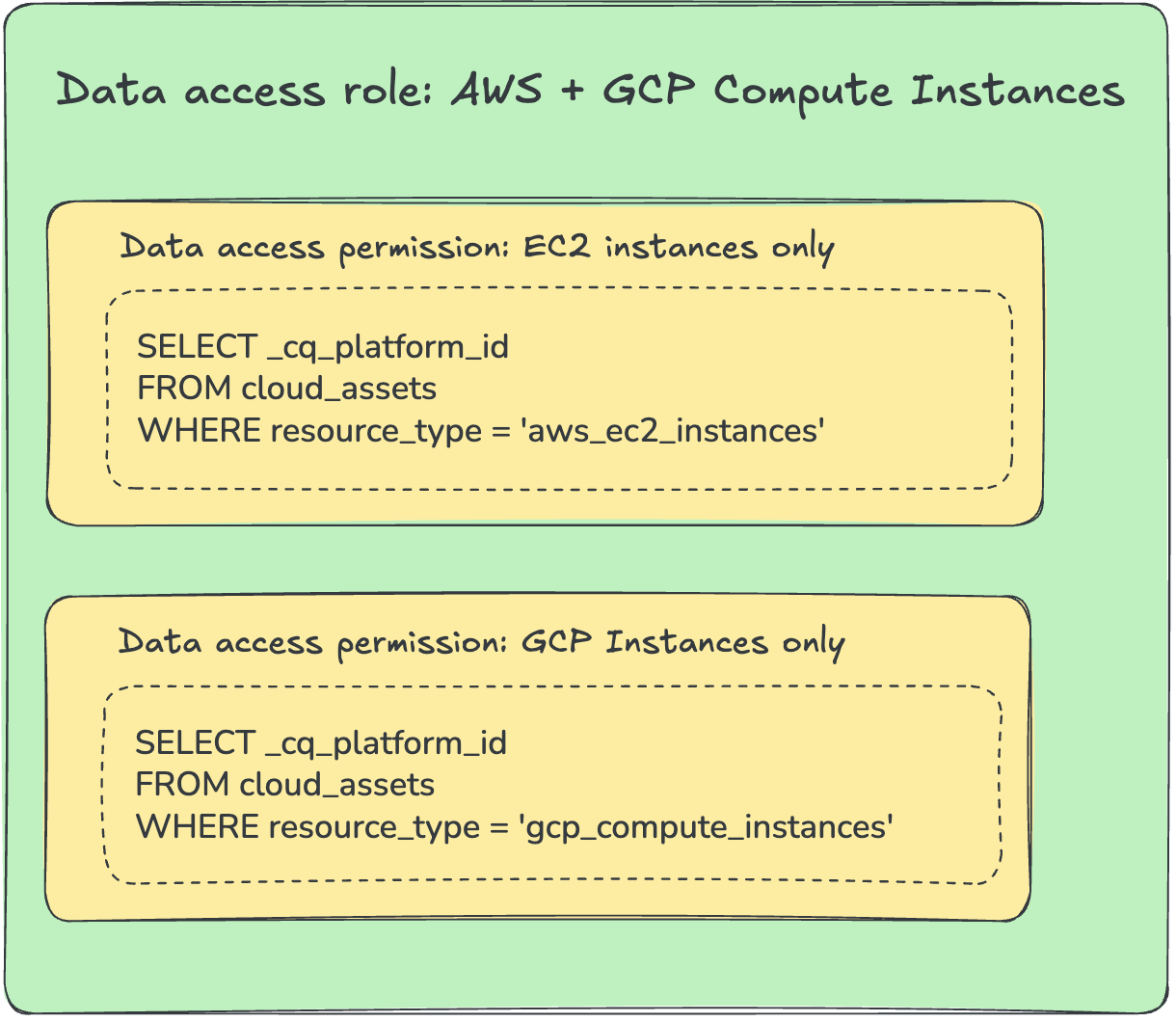
Data Permissions
Data permissions grant access to a subset of data synced to CloudQuery Platform. The data permissions are defined dynamically using SQL as a set of _cq_platform_id values each permission grants access to.
For example, a data permission defined as
SELECT _cq_platform_id
FROM cloud_assets
WHERE resource_type = 'aws_ec2_instances'grants access to data about all EC2 instances, but nothing else.
Data Access Roles
Data Access Roles are a special case of the GENERAL:READ role that represent a collection of one or more Data Access Permissions. The roles can be assigned to manually users in the User Management, or automatically using SSO identity provider. A user can have multiple data access roles assigned. However, for the roles to have an effect, the user must not have any of the built-in roles assigned.
For a Data Access Role to have any effect, the user must not have any built-in role assigned. The Data Access Roles automatically inherit all permissions from the General:Read role.
Configuring Data Access from scratch
Planning
Here are a few things to consider when planning what user roles to use on CloudQuery Platform to limit access to the data:
-
What is the primary criteria you want to distinguish by? Is it available on all assets? For example, if you decide to limit access by region, not all assets actually have a region available and you may need to include them in the data access permissions in another way.
-
What granularity do you require for the data access permissions? You can have 1-1 mapping of permissions to roles, or you can make them very granular and then use various combinations of permissions in the Data Access Roles.
-
Are you going to need to restrict access to some specific data? Data Access Permissions are inclusive, meaning you cannot restrict access to specific assets with one Data Access Permission once it is granted with another one for the same role.
Defining the data permission
Data Access Permissions rely on the _cq_platform_id of assets, which are deterministic unique identifiers of all resources in the Platform database. The Permissions are defined as SQL queries returning the set of the identifiers in the _cq_platform_id column.
For most of the use cases, you should be able to rely on the cloud_assets view to define the permissions, but you can combine it with arbitrary tables available on the platform. For example, to create a Data Access Permission that grants access only to AWS EC2 Instances in the us-east-1 region, you can specify the permission either as
SELECT _cq_platform_id, region FROM aws_ec2_instances
WHERE region='us-east-1'or
select _cq_platform_id from cloud_assets where region = 'us-east-1'
and resource_type='aws_ec2_instances'To create a new Data Access Permission, navigate to Organization Settings > Data permissions. Click the Add data permission button and then fill in the name and description.
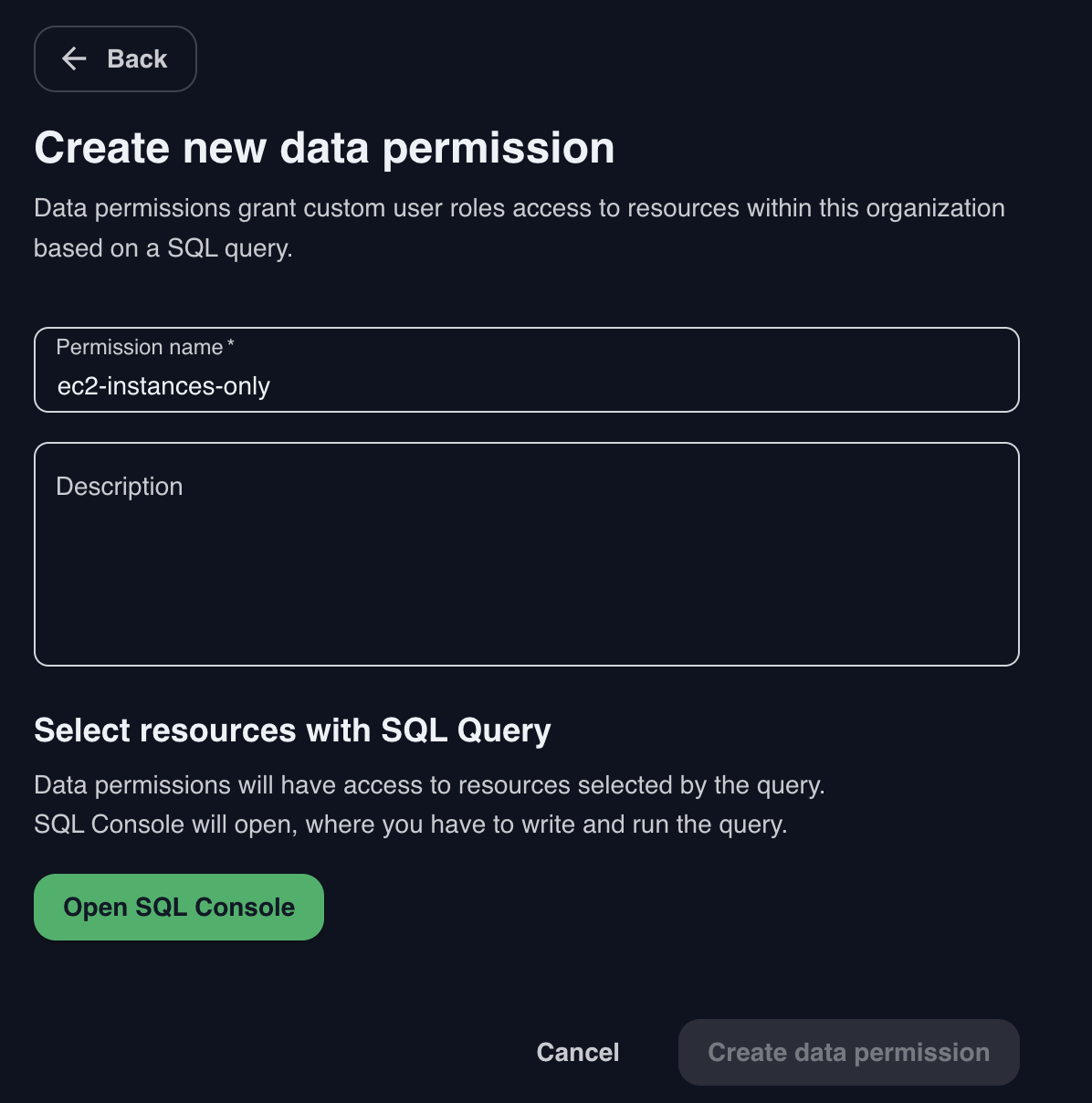
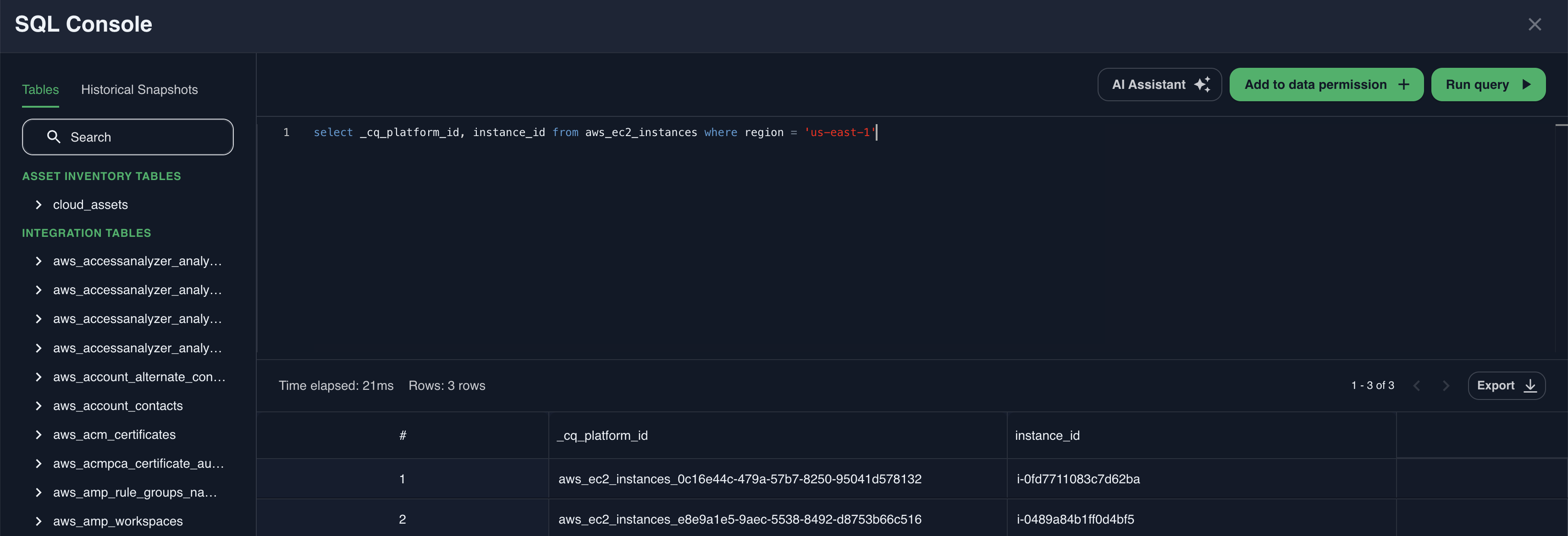
Click the Open SQL Console button to start defining the SQL query for this permission. The SQL Console will open in its Data Access Permissions definition mode (identified by the Add to data permission button in the top right).
Write the query and execute it. The Console will warn you if the resulting table does not use the _cq_platform_id column. Note that you cannot name an arbitrary column as _cq_platform_id, you need to use the column from the database.
You should see the results of the query in the bottom part of the screen. These are the assets the permission will grant the access to.
When ready, click the Add data permission button and you’ll be taken back to the Data Access Permission screen. As a confirmation, you will see the count of resources this permission currently grants access to. To change the query, click the Edit Query button.
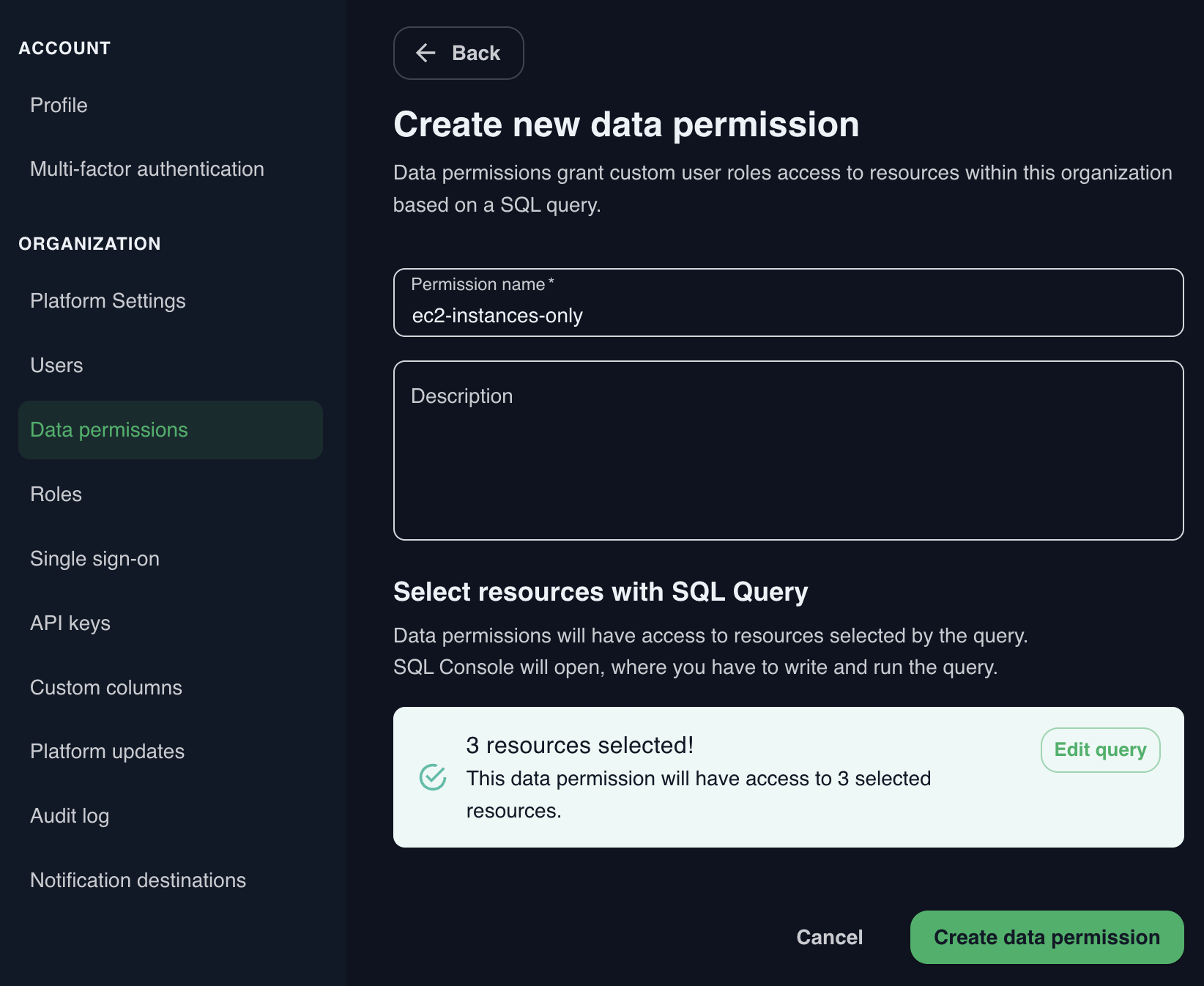
Confirm creation of the Data Access Permission by clicking the Create data permission button.
Next, you need to assign the permission to a Role.
Defining the role
To create a new Data Access Role, navigate to Organization Settings > Roles. Click the Add role button and then fill in the name and description.
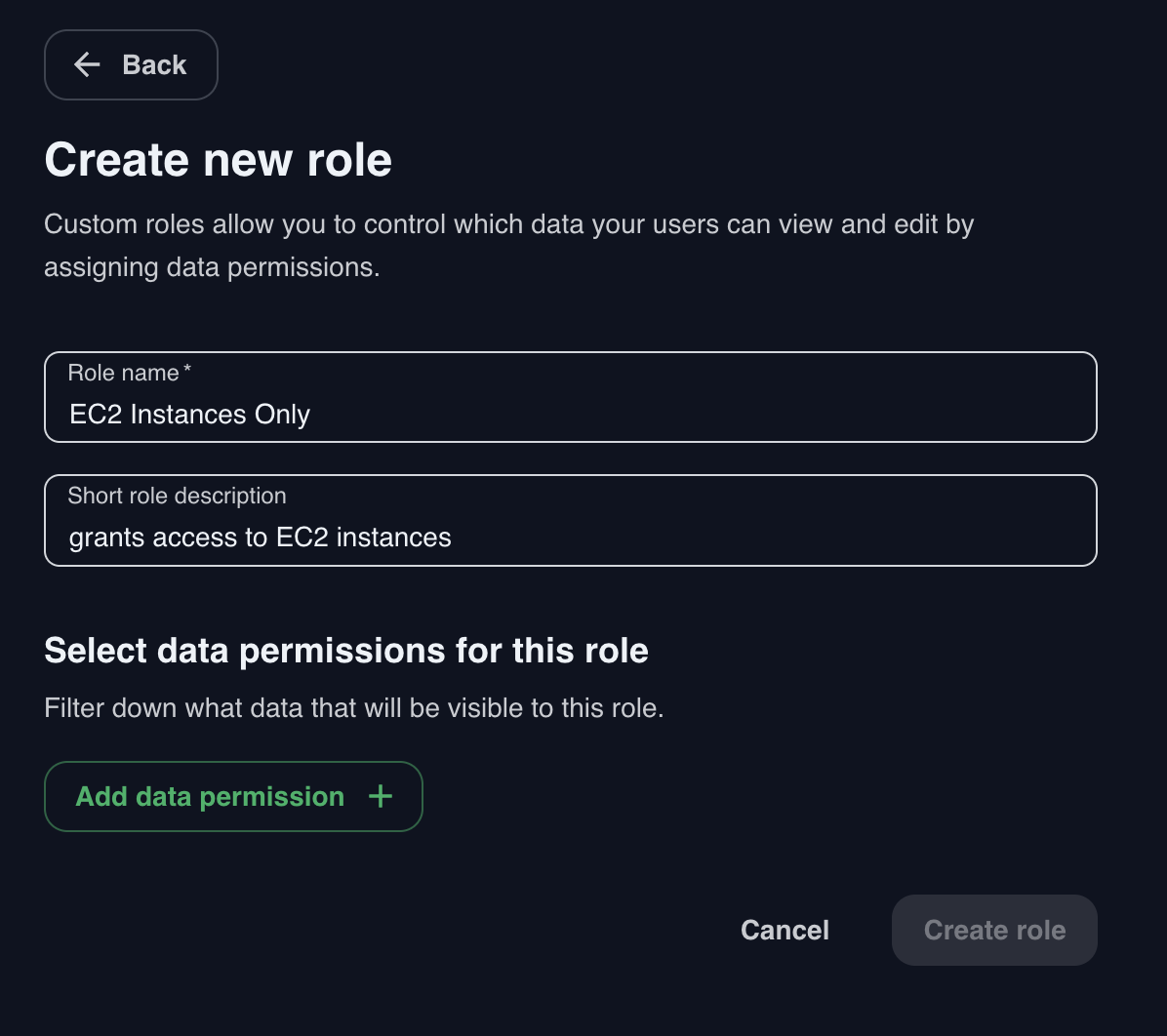
Click the Add Data Permission button and select the permission to be added to this role from the right panel. You can select and add multiple permissions at the same time.
Click Add selected data permissions button and then finish the creation of the role with the Create Role button.
Next, you need to assign the role to a user. If your users log in using Single sign-on, you will need to Map Groups to User Roles . Otherwise, see Changing Non-SSO User’s Workspace Role.