GCP GKE
CloudQuery Platform currently supports integration with GCP Google Kubernetes Engine (GKE). This guide explains the required GCP account setup and configuration steps needed to enable CloudQuery to access your GKE clusters and run sync.
Prerequisites
First, follow the GCP integration setup guide, to create a service account, also assign Kubernetes Engine Viewer role to the service account. Follow the guide to download the JSON key file, which we will use shortly.
Creating K8s integration
- Navigate to Data Pipelines → Integrations in CloudQuery Platform
- Click Create Integration and select K8s
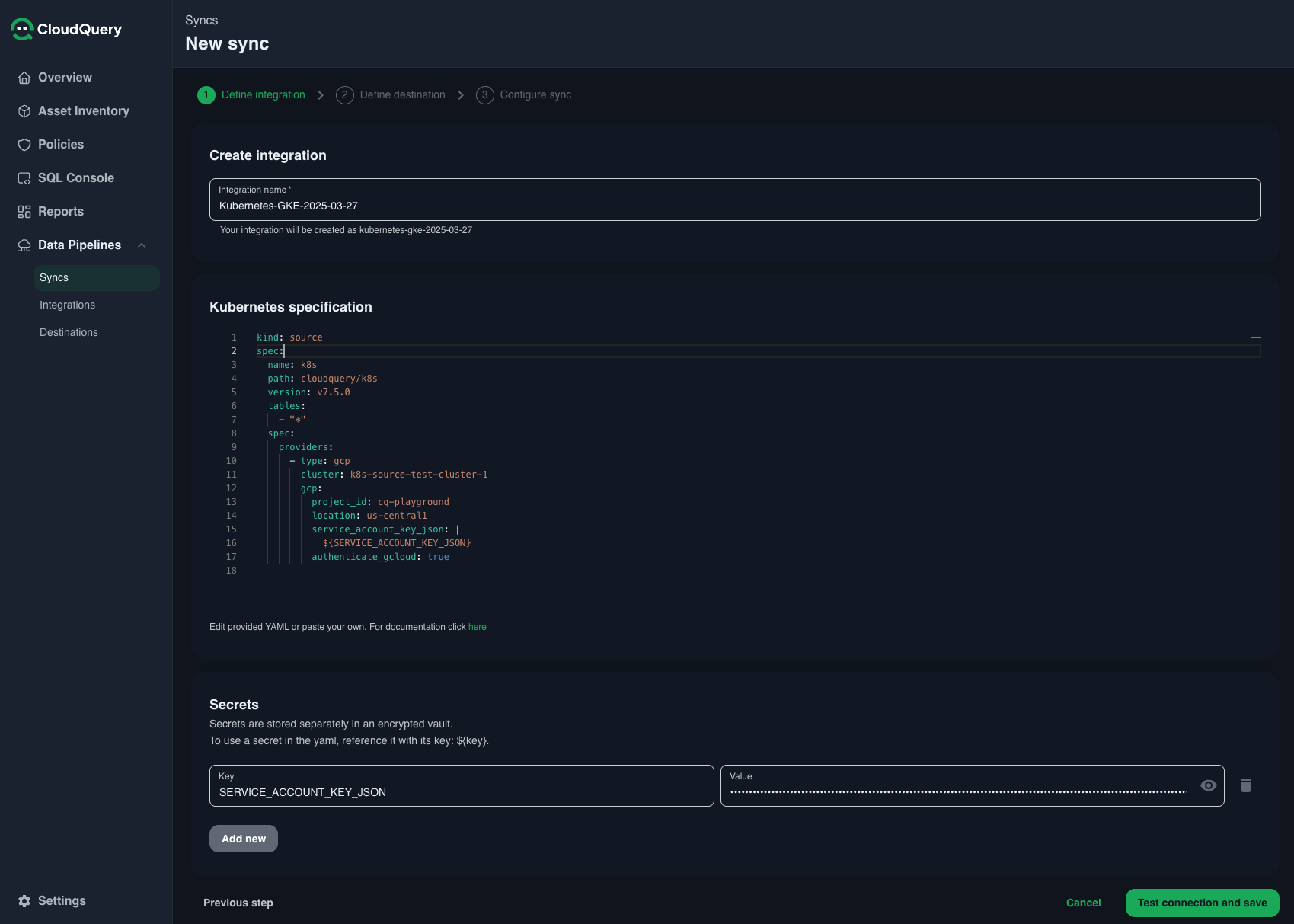
Update the YAML configuration with your cluster details:
kind: source
spec:
name: k8s
path: cloudquery/k8s
version: v7.6.0 # latest version of source k8s plugin
tables:
- "*"
spec:
providers:
- cluster: <cluster-name>
gcp:
authenticate_gcloud: true
location: <cluster-location>
project_id: <project-id>
service_account_key_json: |
${SERVICE_ACCOUNT_KEY_JSON}And add contents of the JSON file downloaded during setup as the secret value for SERVICE_ACCOUNT_KEY_JSON
Replace the <variables> with the correct values from your GCP account and GKE cluster you want to sync.
Optional: Adding permissions to read cluster secrets
By default, the Kubernetes Engine Viewer role will not allow reading cluster secrets, the service account permissions can be modified to read the secrets as well, either by assigning the Kubernetes Engine Admin role, or creating a custom role with container.secrets.list permission.