Azure AKS
CloudQuery Platform currently supports integration with Azure Kubernetes Service (AKS). This guide explains the required AWS account setup and configuration steps needed to enable CloudQuery to access your AKS clusters and run sync.
Prerequisites
First, follow the Azure integration setup guide to create the service principal. This will establish the access needed for CloudQuery to interact with your AKS resources.
Configure AKS Cluster Access
Granting the Cluster Access can be achieved by assigning the Azure Kubernetes Service Cluster User Role to the Service Principal created in the setup guide linked above.
If using the CLI, that can be done using the following command:
# Register the security provider
az role assignment create \
--assignee "{APP_ID}" \
--role "Azure Kubernetes Service Cluster User Role" \
--scope "/subscriptions/{SUBSCRIPTION_ID}"Creating K8s Integration
- Navigate to Data Pipelines → Integrations in CloudQuery Platform
- Click Create Integration and select K8s
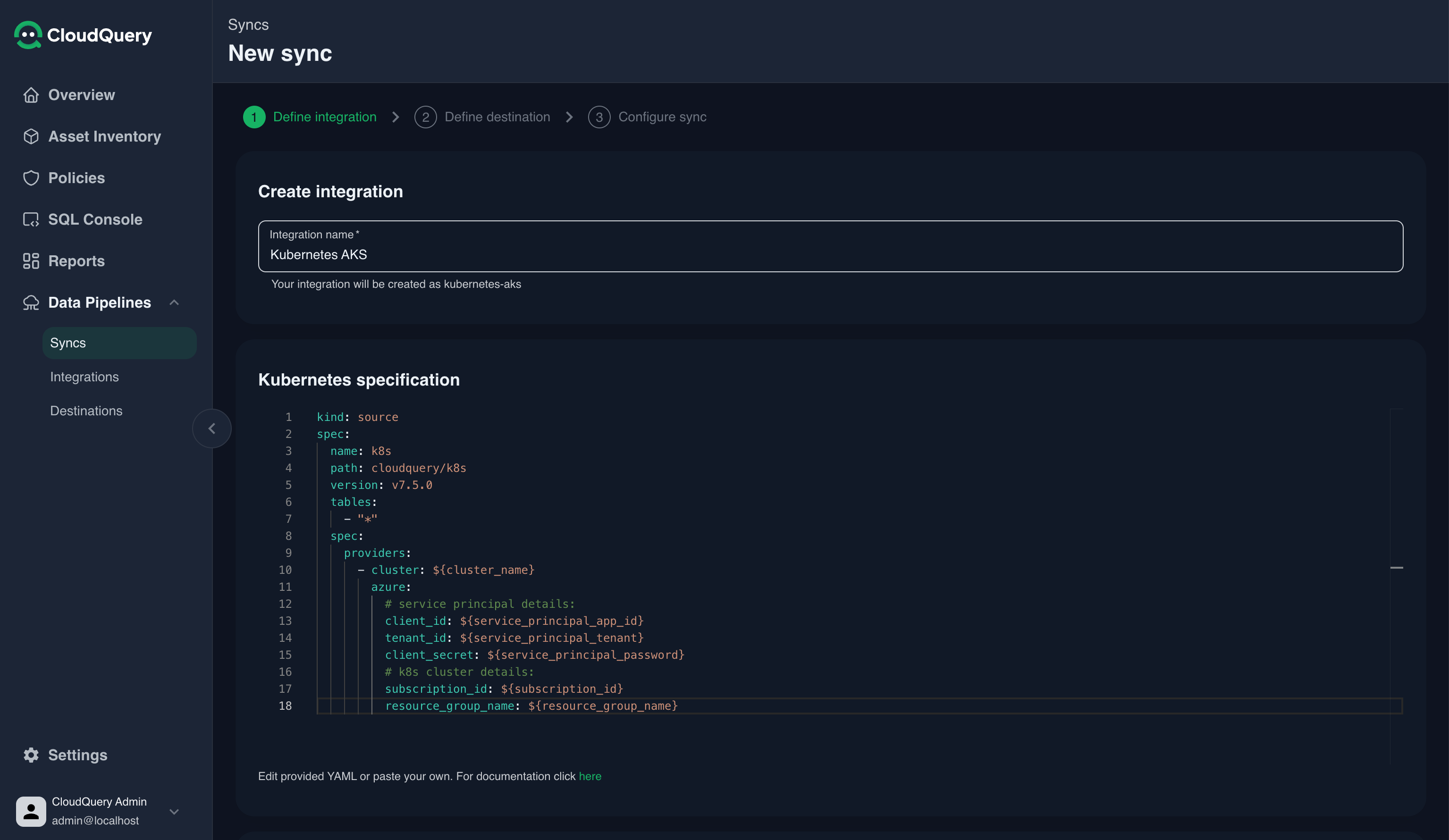
- Update the YAML configuration with your cluster details:
kind: source
spec:
name: k8s
path: cloudquery/k8s
version: v7.6.0 # latest version of source k8s plugin
tables:
- "*"
spec:
providers:
- cluster: ${cluster_name}
azure:
# service principal details:
client_id: ${service_principal_app_id}
tenant_id: ${service_principal_tenant}
client_secret: ${service_principal_password}
# k8s cluster details:
subscription_id: ${subscription_id}
resource_group_name: ${resource_group_name}